Top Conflicts to Watch in 2018
-- Maj gen P K mallick,VSM (Retd)
Center of Preventive Action of Council on Foreign Relation has identified eight conflicts as"top tier" risks In this year 2017. These were:
- military conflict involving the United States, North Korea, and its neighboring countries
- an armed confrontation between Iran and the United States or one of its allies over Iran's involvement in regional conflicts and support of militant proxy groups, including the Yemeni Houthis and Lebanese Hezbollah
- a highly disruptive cyberattack on U.S. critical infrastructure and networks
- a deliberate or unintended military confrontation between Russia and North Atlantic Treaty Organization members, stemming from assertive Russian behavior in Eastern Europe
- an armed confrontation over disputed maritime areas in the South China Sea between China and one or more Southeast Asian claimants—Brunei, Malaysia, the Philippines, Taiwan, or Vietnam
- a mass casualty terrorist attack on the U.S. homeland or a treaty ally by either foreign or homegrown terrorist(s)
- intensified violence in Syria as government forces attempt to regain control over territory, with heightened tensions among external parties to the conflict, including the United States, Russia, and Iran
- increased violence and instability in Afghanistan resulting from the Taliban insurgency and potential government collapse
Many of the contingencies identified in previous surveys remain concerns for 2018. Of the thirty identified this year, twenty-two were considered risks last year. Among the eight new contingencies in this year's survey are the risks of intensified clashes between Israel and Hezbollah, increased violence and political instability in the Sahel region of Africa, and escalating tensions or extremist violence in the Balkans.
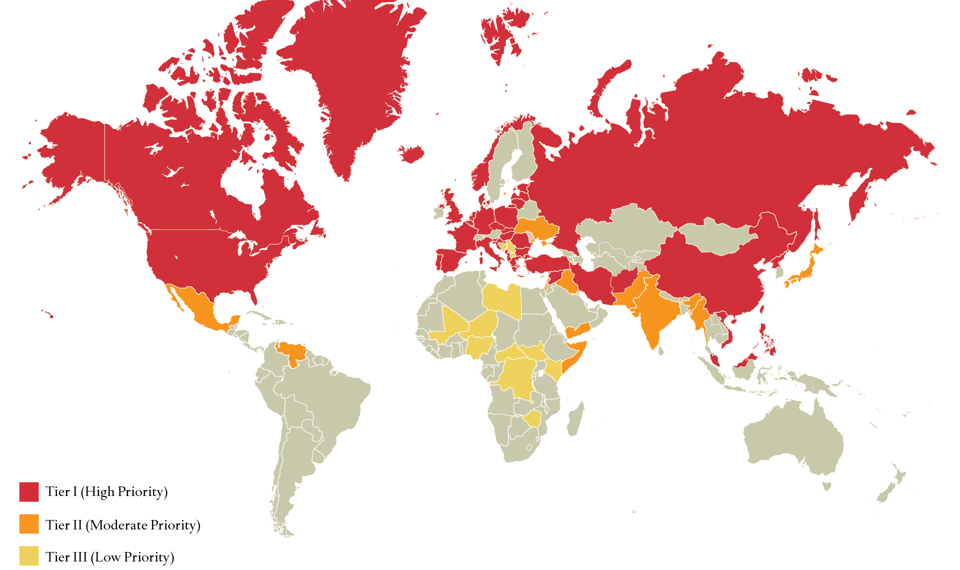
Two contingencies were upgraded to the top tier this year: an armed confrontation between Iran and the United States or one of its allies, and an armed confrontation over disputed maritime areas in the South China Sea between China and one or more Southeast Asian claimants.
The 2018 survey downgraded the priority rankings of two contingencies, compared to last year: the intensification of violence between Turkey and various Kurdish armed groups within Turkey and neighboring countries, and the probability of greater violence in Libya.
Other scenarios in this category include a mass-casualty terrorist attack on the U.S. homeland, a major cyberattack on U.S. critical infrastructure, and two surprising contingencies given how quiet each front was in 2017: military confrontations between Russia and nato members, or between China and one or more Southeast Asian nations over territorial disputes in the South China Sea.










/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/KHKO67JAVNFKRLZR5DQWOJ56GQ.jpg)
/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/2DJTMGIKNRCODNB4X6SQSQKI2Q.jpg)